Data Processing Addendum
℅ Lexer Pty Ltd
80-86 Inkerman Street
St Kilda, Victoria, Australia 3182
privacy@lexer.io
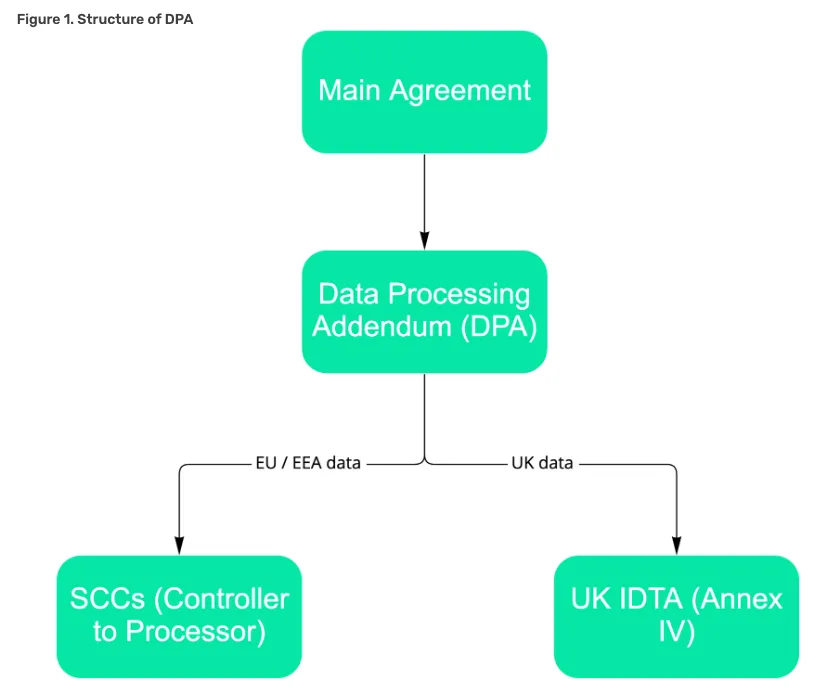
If the Controller requires the additional mandatory Standard Contractual Clauses (SCCs) for EU data subjects, or International Data Transfer Agreement (IDTA) for UK data subjects (refer to Figure 1 below), please submit a request for an addendum to be sent to you via DocuSign
Lexer Pty Ltd will act as the Processor and Service Provider (as defined in Section 1 of the DPA Terms)
All laws, regulations and court orders which apply to the processing of Personal Data in:
- the European Economic Area (‘EEA’)
- the United Kingdom (‘UK’)
- the United States (‘US’)
- Australia
- Singapore
- New Zealand
This includes the European Union Regulation (EU) 2016/679 (‘GDPR’), the Data Protection Act 2018 (‘UK DPA’), California Consumer Privacy Act of 2018 (‘CCPA’), California Privacy Rights Act of 2020 (‘CPRA’)], the Privacy Act 1988 (‘AU PA’), the Personal Data Protection Act 2012 (‘SG PDPA’) and the Privacy Act 2020 (‘NZ PA’), each as amended from time to time.
As described in the Main Agreement.
For the Term of this DPA, and the additional period specified in clause 11.7 of the Main Agreement ('Your Data Portability and Deletion').
The processing of personal data for the purposes of providing the services, as further described in the Main Agreement, including, for the avoidance of doubt, to provide the Controller with, and update and improve, Lexer’s services (or as otherwise agreed in writing by the parties).
The frequency of data transfer depends on the type of data. The range of frequency is between real-time and quarterly, depending on the data. Most data is transferred at least daily.
The types of personal data processed are:
- Name
- Address
- Date of birth
- Gender / inferred gender
- Purchase history
- Commercial behaviour characteristics
- Any other data specified in a Work Order
The individuals whose Personal Data will be processed are end user customers and prospects of the Controller.
For EU Data Subjects: The Standard Contractual Clauses approved by the European Commission Decision of 4 June 2021 (as amended from time to time), for the transfer of personal data from the EEA or adequate country to a third country, as shown in Figure 1 below.
For UK Data Subjects: International Data Transfer Addendum issued by the Information Commissioner’s Office under Section 119A of the Data Protection Act 2018, effective from 21 March 2022 (see Annex IV of Lexer’s Standard Contractual Clauses version). See Figure 1 below.
Technical and organisational measures to ensure the security of Personal Data
For processors requiring EU resident and UK data subject protection under the Standard Contractual Clauses or UK IDTA (see Figure 1 below), Annex II of the Standard Contractual Clauses may also list the technical and organisational security measures.
Current sub-processors
DPA Terms
1. What is this agreement about?
2. What are each party’s obligations?
3. Sub-processing
4. International Personal Data transfers
5. Other important information
6. Privacy and security
7. Audit
Schedule 1: Standard Contractual Clauses
The standard contractual clauses between data controllers and data processors adopted by the European Commission in its Implementing Decision (EU) 2021/91 of 4 June 2021, and currently located here (SCCs) Throughout these SCCs, some are specified as optional. These Variables below specify which optional Clauses are incorporated into these Clauses between the Parties.
Variables
(See Clause 7)
(See Clause 9(a))
The time period referenced in this Clause is 14 days
(See Clause 11(a))
(See Clause 12)
(See Clause 17)
(See Clause 18.2.)
(See Annex IV)
SCC Appendix
ANNEX I
Data exporter(s):
Identify the competent supervisory authority/ies in accordance with Clause 13 of the SCCs:
If the Data Exporter is established an EU Member State: the supervisory authority will be the relevant supervisory body of that Member State.
If the Data Exporter is not established in an EU Member State, but falls within the territorial scope and has appointed a representative pursuant to Article 27(1) of Regulation (EU) 2016/679: The supervisory authority of the Member State in which the representative is established shall act as competent supervisory authority.
If the Data Exporter is not established in an EU Member State, but falls within the territorial scope without having to appoint a representative pursuant to Article 27(2) of Regulation (EU) 2016/679: The supervisory authority of one of the Member States in which the data subjects whose personal data is transferred under these Clauses in relation to the offering of goods or services to them shall act as competent supervisory authority.
ANNEX II
For transfers to (sub-) processors, also describe the specific technical and organisational measures to be taken by the (sub-) processor to be able to provide assistance to the controller and, for transfers from a processor to a sub-processor, to the data exporter
A complete description of Lexer’s security and information security practices are published on our website.
Pseudonymisation: Pseudonymisation is generally not applicable to data processed in the application(s), unless specifically requested by the client and at additional cost.
Encryption: Personal data in application(s) is encrypted in transit and at rest. Personal data is encrypted for transit both to and from the data exporter and for any server-to-server communication necessary for the normal functioning of the application(s). The application(s) uses only private asymmetric keys and prohibits the use of master symmetric keys. Data at rest is encrypted and protected by access controls. Only authenticated users can read, modify, or delete data as specified by the permissions associated with their account.
Confidentiality, integrity and resilience: Disaster recovery plans are in place for all application(s). All employees of processor, by written policy, are provided access on a least-privilege basis and must conduct specialised privacy awareness training.
Restoration availability: Data backups are geo-replicated for applications that store data.
Testing, assessing, evaluating: During each phase of application(s) development, security measures are in place to identify and manage potential vulnerabilities throughout development and release. These include, but are not limited to: OWASP 10 and SANS 25 vulnerabilities, security and privacy risk assessments, third party penetration testing, SOC 2 auditing, ISO27001 certification
User ID and authentication: Features include privilege levels, automatic sign out, failed login restrictions , password based authentication (including using multi-factor authentication), strength and complexity of passwords enforced, passwords stored in encrypted format, single-sign on in certain circumstances where requested by the data exporter as part of their agreement with the processor.
Protection of data in transit: All data is encrypted in transit.
Protection of data in storage: All data is encrypted at rest.
Physical security: Amazon Web Services (AWS) is our sub-processor who processes all personal data and manages physical security of data servers. See Annex III for details.
Ensuring events logging: Security logs capture the following events:
User, system, or process identifier that triggered the event
Description of event
Date and time of event
Authorization information associated with the event
Security logs, which are protected from modification and destruction, are maintained for at least 1 year.
Measures ensuring system configuration: Penetration tests, vulnerability management, peer reviews.
IT security governance and management: The processor maintains an information security management system (ISMS), including risk management, change control, incident management, corrective measures and management oversight.
Measures for certification/assurance of processes and products: ISO27001 certification, SOC 2 reports
Data quality / data retention: Please see the applicable section of processors application agreement.
Ensuring accountability: All employees of processor are trained and must acknowledge processors' cybersecurity policies. Compliance with policy is monitored and refresher training provided annually. Our privacy representative may be contacted by emailing privacy@lexer.io
Data portability / ensuring erasure: Please see the applicable section of processors application agreement.
ANNEX III
The controller has authorised the use of the following sub-processors:
Amazon Web Services (AWS)
The Data Protection Officer can be contacted at aws-EU-privacy@amazon.com
Refer to Annex 1 (Security Standards) of the AWS Data Processing Agreement for further information.
ANNEX IV: UK INTERNATIONAL DATA TRANSFER AGREEMENT (IDTA) ADDENDUM
This Addendum (Annex IV) has been issued by the Information Commissioner for Parties making Restricted Transfers. The Information Commissioner considers that it provides Appropriate Safeguards for Restricted Transfers when it is entered into as a legally binding contract.
Which Parties may end this Addendum as set out in Section 19:
- Importer; and
- Exporter
